Introduction To Kali and WiFi Pen Testing
How to Install Kali Linux
WEP Hacking
Kali Linux and Reaver
Getting a Handshake and a Data Capture, WPA Dictionary Attack
Using Aircrack and a Dictionary to Crack a WPA Data Capture
Cracking a WPA Capture with the GPU using HashCat
Creating a Dictionary / Wordlist with Crunch Part 8
Using Aircrack and a Dictionary to Crack a WPA Data Capture
If you have a WPA handshake capture and cannot crack it yourself then there are services online that for a price will crack it for you.
To get started you should already have a WPA handshake file and Kali Linux running.
Getting a good dictionary can be hard but finding good ones, or creating them yourself with Crunch, is necessary to try and use this method. I have setup adownload section HERE with a WPA wordlist/Dictionaries that can be used if needed.
Keep in mind the dictionary file is only a simple text file that can be edited with any text editing program, such as notepad. Don’t use Microsoft Word or Open Office as they make changes that render a wordlist unusable.
If you know a person well enough you can try and type as many guesses as you can think of in a text file then use that as your dictionary.

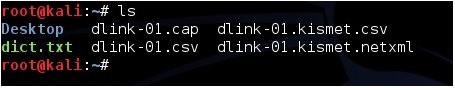
The default storage for a WPA handshake is under /root and will be there under the name it was given when captured. Open a terminal window and type the command “ls” the data capture should be there. The file type we want to use is the .CAP file
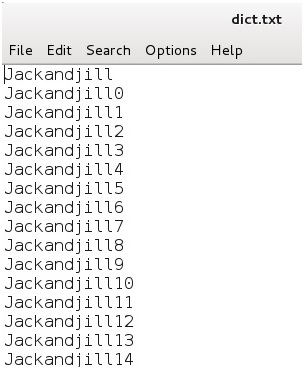
The dictionary that we will use for this example is called dict.txt.

We will be using Aircrack to do the cracking and the command to do this is:
aircrack-ng (file name) -w (dictionary location)
Where the file name is the handshake file that was captured and the dictionary location is the path to the dictionary. The location of where these two files are and their names will be up to you.
The usual default location of the handshake file is under /root and is whatever name it was called when captured. We will be using a dictionary called dict.txt for this example that I copied to /root.
So the command for me to do this would be:
“aircrack-ng dlink.cap -w dict.txt”

If done right Aircrack should start and begin to try to crack the WPA handshake capture with the dictionary.

If the dictionary finds it, it will show as above with the “KEY FOUND” if not, then another dictionary will need to be used. For this example, I edited the text dictionary file and put the password in to show what it looks like when it is found.
How to Install Kali Linux
WEP Hacking
Kali Linux and Reaver
Getting a Handshake and a Data Capture, WPA Dictionary Attack
Using Aircrack and a Dictionary to Crack a WPA Data Capture
Cracking a WPA Capture with the GPU using HashCat
Creating a Dictionary / Wordlist with Crunch Part 8
Using Aircrack and a Dictionary to Crack a WPA Data Capture
If you have a WPA handshake capture and cannot crack it yourself then there are services online that for a price will crack it for you.
To get started you should already have a WPA handshake file and Kali Linux running.
Getting a good dictionary can be hard but finding good ones, or creating them yourself with Crunch, is necessary to try and use this method. I have setup adownload section HERE with a WPA wordlist/Dictionaries that can be used if needed.
Keep in mind the dictionary file is only a simple text file that can be edited with any text editing program, such as notepad. Don’t use Microsoft Word or Open Office as they make changes that render a wordlist unusable.
If you know a person well enough you can try and type as many guesses as you can think of in a text file then use that as your dictionary.
The default storage for a WPA handshake is under /root and will be there under the name it was given when captured. Open a terminal window and type the command “ls” the data capture should be there. The file type we want to use is the .CAP file
The dictionary that we will use for this example is called dict.txt.
We will be using Aircrack to do the cracking and the command to do this is:
aircrack-ng (file name) -w (dictionary location)
Where the file name is the handshake file that was captured and the dictionary location is the path to the dictionary. The location of where these two files are and their names will be up to you.
The usual default location of the handshake file is under /root and is whatever name it was called when captured. We will be using a dictionary called dict.txt for this example that I copied to /root.
So the command for me to do this would be:
“aircrack-ng dlink.cap -w dict.txt”
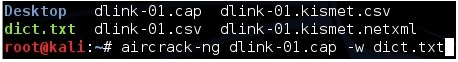
If done right Aircrack should start and begin to try to crack the WPA handshake capture with the dictionary.
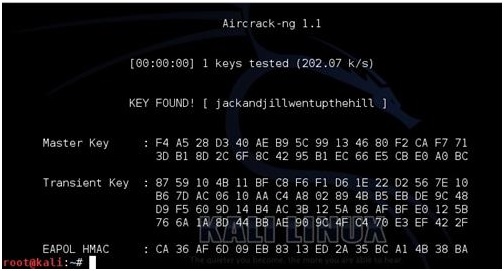
If the dictionary finds it, it will show as above with the “KEY FOUND” if not, then another dictionary will need to be used. For this example, I edited the text dictionary file and put the password in to show what it looks like when it is found.